Q. 5 (A) : Write the comparison Between Dot Matrix Printers & Laser Printers with respect to Print Quality, Speed, Noise and cost parameters.
Answer
Print Quality
A typical laser printer has a resolution of 1,200 dots per
inch, or dpi. It achieves this level of detail through the use of microscopic
toner powder, high-performance electronics and precision optics. Many laser
printers have color capability at the same high resolution. Some dot matrix
printers achieve 240 dpi by making repeated passes over the same printed area,
though documents produced this way take at least twice as long to print as
those printed at normal quality. As a dot matrix printer's output color depends
on the ribbon, virtually none offer choices beyond black and red.
Speed
A typical desktop laser printer turns out about four full-color pages per minute; for black-and-white text, this rises to 25 pages per minute. Dot matrix printers are typically rated at between 200 and 600 characters per second, or about 50 pages per minute in draft mode. Some high-output dot matrix printers achieve 1,100 characters per second, or 100 pages per minute, although the print quality is low-resolution text.
Noise
Dot matrix technology prints by striking an inked ribbon with a column of metal pins. At the speeds required for printing, the pins move very rapidly, producing a loud buzz. Sound-deadening equipment covers reduce the noise to tolerable levels for office use. Laser printers are quiet by comparison. The paper-feed mechanism produces light clicking sounds, but no sound deadening is necessary for a laser printer.
Costs
Laser and dot matrix printers have roughly comparable
initial purchase prices: as of October 2012, dot matrix models run between $250
to $600, and you can find low-end laser printers for under $100, though most
range between $150 to $600. The per-page cost for dot matrix printers is lower,
at .15 to .2 cents per page; laser printers cost from 1 to 9 cents per page.
Dot matrix printers use inexpensive ribbons and have little other maintenance;
however, the toner cartridges used for laser printing figure heavily into
operating costs.
Q. 5 (B) : How to turn off and activate automatic spelling
checking and automatic grammar checking in MS Office programs?
Answer :
You're typing along, you make a mistake, and you see the
wavy red underline.
You fix the mistake, but you've lost your flow, your idea.
To avoid that distraction, you can turn spell check off, then check spelling
manually when you're done writing. Here's how.
Click File > Options > Proofing, clear the
Check spelling as you type box, and click OK.
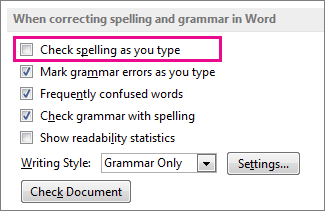
To turn spell check back on, repeat the process and select
the Check spelling as you type box.
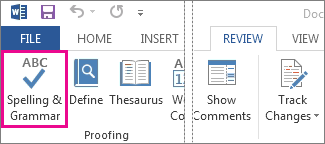
To check spelling manually, click Review > Spelling
& Grammar.
But do remember to run spell check. Spelling and grammar
errors can seriously undermine what you're trying to say, especially when your
boss, your teacher, or that person in HR sees them.
Q. 5 (C ) : What are the Storage Hierarchy? Which is the fastest memory in a computer system? Which is faster, cache or register and why?
Answer
In computer architecture, the memory hierarchy separates
computer storage into a hierarchy based on response time. Since response time,
complexity, and capacity are related, the levels may also be distinguished by
their performance and controlling technologies.[1] Memory hierarchy affects
performance in computer architectural design, algorithm predictions, and lower
level programming constructs involving locality of reference.
Designing for high performance requires considering the
restrictions of the memory hierarchy, i.e. the size and capabilities of each
component. Each of the various components can be viewed as part of a hierarchy
of memories (m1,m2,...,mn) in which each member mi is typically smaller and
faster than the next highest member mi+1 of the hierarchy. To limit waiting by
higher levels, a lower level will respond by filling a buffer and then
signaling for activating the transfer.
There are four major storage levels.
- Internal – Processor registers and cache.
- Main – the system RAM and controller cards.
- On-line mass storage – Secondary storage.
- Off-line bulk storage – Tertiary and Off-line storage.
Q. 6 (A) : Intellectual property (IP) refers to creations of the intellect for which a monopoly is assigned to designated owners by law. What are the ways to protect IP rights?
Answer
Intellectual property (IP)
Intellectual property (IP) is a term referring to creations
of the intellect for which a monopoly is assigned to designated owners by law.
Some common types of intellectual property rights (IPR) are copyright, patents,
and industrial design rights; and the rights that protect trademarks, trade
dress, and in some jurisdictions trade secrets: all these cover music,
literature, and other artistic works; discoveries and inventions; and words,
phrases, symbols, and designs. Intellectual property rights are themselves a
form of property, called intangible property.
How to Protect Intellectual Property by Different Ways
Copyright ©
Copyright applies to the protection of tangible and
intangible creative works. You own the copyright the moment you create
something if you did not register it. However, it will be easier to validate
your ownership, especially in a legal dispute, if you take your time to
register your work.
Trademark ™
Businesses use symbols, designs, logos, and catchphrases as
part of their marketing strategy and identity. It's these images and words that
help a company connect to its customers; thus, these need to be protected from
possible commercial saboteurs who might use or copy the designs for their own economic
gain.
Patent ®
If you've invented a unique product, the machine or
equipment, or chemical composition, you can also protect this IP by filing for
a patent with the USPTO online. Patents carry legal protection that excludes
others from making and distributing your invention unless you have given them
the license. There are different types of the patent process, and the
conditions or requirements depend on the product or
invention so you'll need to carefully identify which category the IP fits best.
Q. 6 (B) ) A database is an organized collection of data. What is relational database? What are the usefulness of primary key, secondary key and stored procedure in relational database?
Relational database
A relational database is a collection of information that
organizes data points with defined relationships for easy access. In the
relational database model, the data structures -- including data tables,
indexes and views -- remain separate from the physical storage, allowing
administrators to edit the physical data storage without affecting the logical
data structure.
The data tables used in a relational database store
information about the related objects. Each row holds a record with a unique
identifier -- known as a key -- and each column contains the attributes of the
data. Each record assigns a value to each feature, making relationships between
data points easy to identify.
Primary Key – A primary is a column or set of columns
in a table that uniquely identifies tuples (rows) in that table.
Super Key – A super key is a set of one of more
columns (attributes) to uniquely identify rows in a table.
Candidate Key – A super key with no redundant attribute is
known as candidate key
Alternate Key – Out of all candidate keys, only one
gets selected as primary key, remaining keys are known as alternate or
secondary keys.
Composite Key – A key that consists of more than one
attribute to uniquely identify rows (also known as records & tuples) in a
table is called composite key.
Foreign Key – Foreign keys are the columns of a table
that points to the primary key of another table. They act as a cross-reference
between tables.
Q 7 (A) : Write step-by-step procedure of Linux booting.
Answer :
Step 1: Power Supply & SMPS
One of the main component of a computer is SMPS(Switching
Mode Power Supply). The primary objective of this component is to provide the
perfect required voltage level to the motherboard and other computer
components. Computer internals work in DC, however the power supply we have at
home and other places are AC. SMPS converts AC to DC and maintain the required
voltage level so that the computer can work flawlessly.
Step 2: Bootstrapping
Something has to be programmed by default, so that the CPU
knows where to search for instructions.
Step 3: The Role of BIOS in booting process
The word booting comes from another word called
bootstrapping. The computer knows how to bring itself up, when you press the
start button, because of the instructions that are fed to a program called as
BIOS. BIOS stands for Basic Input Output System. The most important use of BIOS
during the booting process is POST. POST stands for Power on Self Test. Its a
series of tests conducted by the bios, which confirms the proper functioning of
different hardware components attached to the computer.
Step 4: MBR and GRUB
Now as you don't have any bootable CD in your CD ROM Drive,
the bios will look at the second device from the boot order settings. The
second device is your Hard Disk.
Step 5 Loading The kernel Image
Similar to GRUB, kernel is also loaded in stages. A linux
kernel is responsible for handling Process management, Memory Management,
Users, Inter process communication etc. I must say kernel is never used by a
user. What the kernel does is to maintain a good environment for programs to
run. Yeah we use kernel thrugh different programs.
Q.7 (B) : In the Linux file structure files are grouped according to purpose. What are groups and their purpose of file structure of Linux system?
Answer :
1. / – Root
Every single file and directory starts from the root
directory.
Only root user has write privilege under this directory.
Please note that /root is root user’s home directory, which
is not same as /.
2. /bin – User Binaries
Contains binary executables.
Common linux commands you need to use in single-user modes
are located under this directory.
Commands used by all the users of the system are located
here.
For example: ps, ls, ping, grep, cp.
3. /sbin – System Binaries
Just like /bin, /sbin also contains binary executables.
But, the linux commands located under this directory are
used typically by system aministrator, for system maintenance purpose.
For example: iptables, reboot, fdisk, ifconfig, swapon
4. /etc – Configuration Files
Contains configuration files required by all programs.
This also contains startup and shutdown shell scripts used
to start/stop individual programs.
For example: /etc/resolv.conf, /etc/logrotate.conf
5. /dev – Device Files
Contains device files.
These include terminal devices, usb, or any device attached
to the system.
For example: /dev/tty1, /dev/usbmon0
6. /proc – Process Information
Contains information about system process.
This is a pseudo filesystem contains information about
running process. For example: /proc/{pid} directory contains information about
the process with that particular pid.
This is a virtual filesystem with text information about
system resources. For example: /proc/uptime
7. /var – Variable Files
var stands for variable files.
Content of the files that are expected to grow can be found
under this directory.
This includes — system log files (/var/log); packages and
database files (/var/lib); emails (/var/mail); print queues (/var/spool); lock
files (/var/lock); temp files needed across reboots (/var/tmp);
8. /tmp – Temporary Files
Directory that contains temporary files created by system
and users.
Files under this directory are deleted when system is
rebooted.
9. /usr – User Programs
Contains binaries, libraries, documentation, and source-code
for second level programs.
/usr/bin contains binary files for user programs. If you
can’t find a user binary under /bin, look under /usr/bin. For example: at, awk,
cc, less, scp
/usr/sbin contains binary files for system administrators.
If you can’t find a system binary under /sbin, look under /usr/sbin. For
example: atd, cron, sshd, useradd, userdel
/usr/lib contains libraries for /usr/bin and /usr/sbin
/usr/local contains users programs that you install from
source. For example, when you install apache from source, it goes under
/usr/local/apache2
10. /home – Home Directories
Home directories for all users to store their personal
files.
For example: /home/john, /home/nikita
11. /boot – Boot Loader Files
Contains boot loader related files.
Kernel initrd, vmlinux, grub files are located under /boot
For example: initrd.img-2.6.32-24-generic,
vmlinuz-2.6.32-24-generic
12. /lib – System Libraries
Contains library files that supports the binaries located
under /bin and /sbin
Library filenames are either ld* or lib*.so.*
For example: ld-2.11.1.so, libncurses.so.5.7
13. /opt – Optional add-on Applications
opt stands for optional.
Contains add-on applications from individual vendors.
add-on applications should be installed under either /opt/
or /opt/ sub-directory.
14. /mnt – Mount Directory
Temporary mount directory where sysadmins can mount
filesystems.
15. /media – Removable Media Devices
Temporary mount directory for removable devices.
For examples, /media/cdrom for CD-ROM; /media/floppy for
floppy drives; /media/cdrecorder for CD writer
16. /srv – Service Data
srv stands for service.
Contains server specific services related data.
For example, /srv/cvs contains CVS related data.
Q. 8 (A) : By taking suitable example, explain how decimal number is converted into binary number.
Answer :
Steps for Decimal to Binary Conversion
Step – 1 Divide the decimal number which is to be
converted by two which is the base of the binary number.
Step – 2 The remainder which is obtained from step 1
is the least significant bit of the new binary number.
Step – 3 Divide the quotient which is obtained from
the step 2 and the remainder obtained from this is the second least significant
bit of the binary number.
Step – 4 Repeat the process until the quotient
remains zero.
Step – 5 The last remainder obtained from the
division is the most significant bit of the binary number. Hence arrange the
number from most significant bit to the least significant bit (i.e., from
bottom to top).
This method can easily be understood by considering an
example which is explained below.
For example – Consider the conversion of the decimal number
25 into its equivalent binary.
Q. 8 (B) : How to manage disk partitions on windows using inbuilt disk management tool.
Answer :
The easiest way to access Windows 7 Disk Management:
Right click "Computer"→ select "Manage"
→ Get the new control panel, open "Storage" and choose "Disk
Management" in submenu, and then you will get the following Disk
Management:
Other three ways to get Windows Disk Management in Windows 7
Click "Start" → "Control Panel"
→ "System and Security" → "Administrative Tools",
then double-click the "Computer Management" → "Disk
Management"
Click "Start". Type "diskmgmt.msc"
in the text box and then click "Enter"
Click "Start" → "Control Panel",
search "partition" in the Control Panel, and then choose
Create and Format Hard Disk Partitions.
c) Explain the following terms:
[I] : System Software
Answer :
system software
System software is a type of computer program that is
designed to run a computer’s hardware and application programs. If we think of
the computer system as a layered model, the system software is the interface
between the hardware and user applications. The operating system (OS) is the
best-known example of system software. The OS manages all the other programs in
a computer.
Other examples of system software include:
- The BIOS (basic input/output system) gets the computer system started after you turn it on and manages the data flow between the operating system and attached devices such as the hard disk, video adapter, keyboard, mouse and printer.
- The boot program loads the operating system into the computer's main memory or random access memory (RAM).
- An assembler takes basic computer instructions and converts them into a pattern of bits that the computer's processor can use to perform its basic operations.
- A device driver controls a particular type of device that is attached to your computer, such as a keyboard or a mouse. The driver program converts the more general input/output instructions of the operating system to messages that the device type can understand.
8. c) Explain the following terms:
[I] : Application Software
One of the first things to understand about the term “application software” is that it is exceedingly broad.
Application software is commonly defined as any program or
number of programs designed for end-users. That’s it, in a nutshell.
In that sense, any end user program can be called an
“application.” Hence the age-old saying: “there's an app for that.”
People often use the term “application software” to talk
about bundles or groups of individual software applications, using a different
term, “application program,” to refer to individual applications.
That’s because the word “program” correlates to a discrete,
countable single unit, while the word “software” is often used to refer to more
than one individual program.
8. c) Explain the following terms:
[III] : Application Software
A compiler is a program that translates a source program
written in some high-level programming language (such as Java) into machine
code for some computer architecture (such as the Intel Pentium architecture).
The generated machine code can be later executed many times against different
data each time.
An interpreter reads an executable source program written in
a high-level programming language as well as data for this program, and it runs
the program against the data to produce some results. One example is the Unix
shell interpreter, which runs operating system commands interactively.
Note that both interpreters and compilers (like any other
program) are written in some high-level programming language (which may be
different from the language they accept) and they are translated into machine
code. For a example, a Java interpreter can be completely written in C, or even
Java. The interpreter source program is machine independent since it does not
generate machine code. (Note the difference between generate and translated
into machine code.) An interpreter is generally slower than a compiler because
it processes and interprets each statement in a program as many times as the
number of the evaluations of this statement. For example, when a for-loop is
interpreted, the statements inside the for-loop body will be analyzed and
evaluated on every loop step. Some languages, such as Java and Lisp, come with
both an interpreter and a compiler. Java source programs (Java classes with
.java extension) are translated by the javac compiler into byte-code files
(with .class extension). The Java interpreter, called the Java Virtual Machine
(JVM), may actually interpret byte codes directly or may internally compile
them to machine code and then execute that code (JIT: just-in-time
compilation).
Q. 9 (A) : What is a path? What is an absolute and relative path in Linux environment?
Answer :
Path
Alternatively known as the pathname, the current path or
path is the complete location or name of where a computer, file, device, or web
page is located. Below are some examples of different types of computer-related
paths.
Absolute Path
An absolute path is defined as the specifying the location
of a file or directory from the root directory(/).
To write an absolute path-name:
Start at the root directory ( / ) and work down.
Write a slash ( / ) after every directory name (last one is
optional)
For Example : $cat abc.sql
Relative Path
Relative path is defined as the path related to the present
working directly(pwd). It starts at your current directory and never starts
with a / .
To be more specific let’s take a look on the below figure in
which if we are looking for photos then absolute path for it will be provided
as /home/jono/photos but assuming that we are already present in jono directory
then the relative path for the same can be written as simple photos.
UNIX offers a shortcut in the relative pathname– that uses
either the current or parent directory as reference and specifies the path
relative to it. A relative path-name uses one of these cryptic symbols:
.(a single dot) - this represents the current directory.
..(two dots) - this represents the parent directory.
Q. 9 (A) : What is a path? What is an absolute and relative
path in Linux environment?
Answer :
Path
PATH is an environment variable on Unix-like operating
systems, DOS, and Microsoft Windows, specifying a set of directories where
executable programs are located. In general, each executing process or user
session has its own PATH setting.
Absolute path
An absolute path is defined as specifying the location of a
file or directory from the root directory(/). In other words,we can say that an
absolute path is a complete path from start of actual file system from /
directory.
cat /home/kt/abc.sql
Relative path
Relative path is defined as the path related to the present
working directly(pwd). It starts at your current directory and never starts
with a / .
/home/jono/photos
Q. 9 (B) : What is an array formula in Excel? By taking
suitable data, explain sum operation on array of
data.
Answer :
An array formula is a formula that can perform multiple
calculations on one or more items in an array. You can think of an array as a
row or column of values, or a combination of rows and columns of values. Array
formulas can return either multiple results, or a single result.
Syntax :
={formula}
={SUM(LEN(A1:A5))}
=SUMPRODUCT(LEN(A1:A5))
Q. 9 (C) : How Information Technology is going to impact Indian Railways?
Answer :
IT projects which have been carried out and benefiting
Indian Railways
1. Unreserved Ticketing System: UTS started with a launch of a pilot project in 2002 at Northern Railway and today implemented to handle almost 6000 locations and 90% of the total ticket sold every day. This has facilitated not only availability of ticket at all time replacing SPTM but also management of unreserved travel data.
Passenger Reservation System: Reserved travel by Indian
Railways is facilitated by the Passenger Reservation System (PRS) making a
commencement in the year 1988-89. PRS provides reservation services to nearly
2.2 million passengers a day on over 2500 trains running throughout
the country. The PRS Application CONCERT (Countrywide Network of Computerized
Enhanced Reservation and Ticketing) is the world’s largest online reservation
application, prepared and maintained by CRIS. There are 44- Quota, 8-trains, 9
– classes, 162-concession and 127-coaches that make the system very complex and
makes CRIS proud of managing the system so effectively.
Control Office Automation: The train operation over Indian
Railways is monitored and checked through a Control office located in each
Division. The charting of train run was done by color pen and a scale with
manual calculation of time, distance and other parameters. With automation
implemented, the controller only feeds the timings of passing a station and
charting is done automatically. All performance parameters involving
punctuality, average speed, GTKM, NTKM and PKM etc. are worked out immediately.
Freight Operation Information System: The Indian Railways
carry more than 1.1 Billion metric tons of payload per year with nearly 5000
freight trains daily. The Freight Operations Information System (FOIS)
was the first project, which CRIS embarked upon. In fact the creation of CRIS
is a by product of this effort in the mid eighties. FOIS began as an diligence
to track and monitor the movement of wagons, locomotives and unit trains. Now
it is a complete management module for freight trains handling the billing and
revenue collections as well.
Integrated Coaching Management System: There are about 50000
passenger coaches forming a train with assigned composition. ICMS had made this
daily exercise very simple with all performance parameters related to coaching
operation worked out quickly facilitating improvement strategy.
National Train Enquiry System: NTES are integrated with ICMS
to interface with passenger to communicate him passenger related relevant
information such as current running, schedule timings, departure and arrival
etc. This served the passenger knowing the running of train online and can
avoid wastage of time at the station waiting for train running late.
Crew Management System: The crew of the train consists of a
Loco Pilot, Assistant Loco Pilot and Guard. Crew works a trains from station A
to B and then works back the train involving interchange from one division/zone
to another. CMS has facilitated complete data management on system from signing
on to off and all information on click of the mouse. This involved huge
networking of 10-15 crew lobbies in each Zonal Railways.
Software Aided Training School: No Information technology
can work effectively unless the user is trained to keep up and use the assets.
There are many other software introduced at zonal railways
such as Material Management information system, PRIME and AFRESH etc. looking
after the material, personal and finance of the railway.







No comments:
Post a Comment